McAfee is a leading and trusted brand in the security software industry. It was established in the year 1987 by John McAfee.

Everybody who is even the tiniest bit digitally aware knows the importance of antivirus. With so many viruses and other threats lurking around, it is vital to safeguard the network and devices.
McAfee AntiVirus runs in the background and does not cause any hindrance nor slows down the computer. McAfee security suite blocks viruses and other malicious software from entering the computer, and it removes all existing malware from the computer. To setup McAfee on your computer, go to “www.mcafee.com/activate“.
Since malware has the same sorts of codes, McAfee reserves these malware fingerprints in an exhaustive database to identify the threat s soon as it penetrates the device. It is troublesome to hunt malware as attackers design variants of it by attaching on to or altering the real malware signatures.
McAfee defends the machine from malicious software with the help of malware signature. McAfee gives real-time security which indicates that it supplies automated protection. It is a kind of scanning system which essentially monitors the device for any shady movement in real time.
More Helpful Tools for Internet security & privacy online!
- Bitdefender Internet Security: Best McAfee antivirus alternative
- Kaspersky Internet Security: Best antivirus software for Mac
- Kaspersky Anti-Virus: Best antivirus software for windows
- Virtual Private Network (VPN) – NordVPN: #1 VPN for privacy
- Encrypted Cloud Storage – Tresorit: End-to-End Encrypted Cloud Storage
- Firefox: Browser for privacy & Tor: Browse for anonymity
- Private Proxies Resources: Proxies for online anonymous and secure Needs
- DuckDuckGo – #1 search engines for online privacy
How To Uninstall McAfee Setup?
Before installing a new McAfee product, you have to ensure that the new software will not cause conflicts. Therefore, you need to ensure that an older McAfee product is not installed on the device. You should go to the Control Panel and uninstall the more former McAfee product, even if it is expired. After that, download any removal tool and remove the setup entirely. Here is how you can uninstall McAfee product from your computer system:
- Launch the Start menu.
- Click on Control Panel.
- Go to Programs and Features.
- After that, click on Uninstall A Program.
- A list of all the installed programs on the device will get displayed.
- Locate the McAfee program.
- Click on uninstall.
- Restart your computer when the reinstallation is complete.
How To Download McAfee Antivirus Setup?
Interested people can buy the McAfee security suite from either the web or any retail store. After purchasing the product, what next? Now, you have to download the setup. Here is how you can download McAfee setup:
- Launch the Internet browser and go to “www.mcafee.com/activate“
- Sign in to the McAfee user account
- If you do not have an account, then click on the Signup button.
- Register yourself on the McAfee account by furnishing the required details.
- Sign in using the username and password.
- After logging in, go to the homepage.
- Now, locate the McAfee product.
- Click on the download button.
- Go through the McAfee license agreement and click on the Agree button to proceed.
- The download process will be over in a few minutes.
How to install McAfee antivirus?
Now that you have downloaded the setup file, you can continue with the installation process. Make sure that your Operating System is up to date and install all the latest available system drivers. Here is how you can install the McAfee antivirus setup on your computer:
- Go to the default download location folder on your computer.
- If you have downloaded the McAfee setup file elsewhere, then go to that location.
- Find the setup file of McAfee and double-click on it.
- Now, run the file depending on the web browser you are working on.
- Running the executable file will automatically initiate the download process.
- Click on the Install button.
- Click on the Next button.
- Follow the instructions given on the screen.
- Click on close when done.
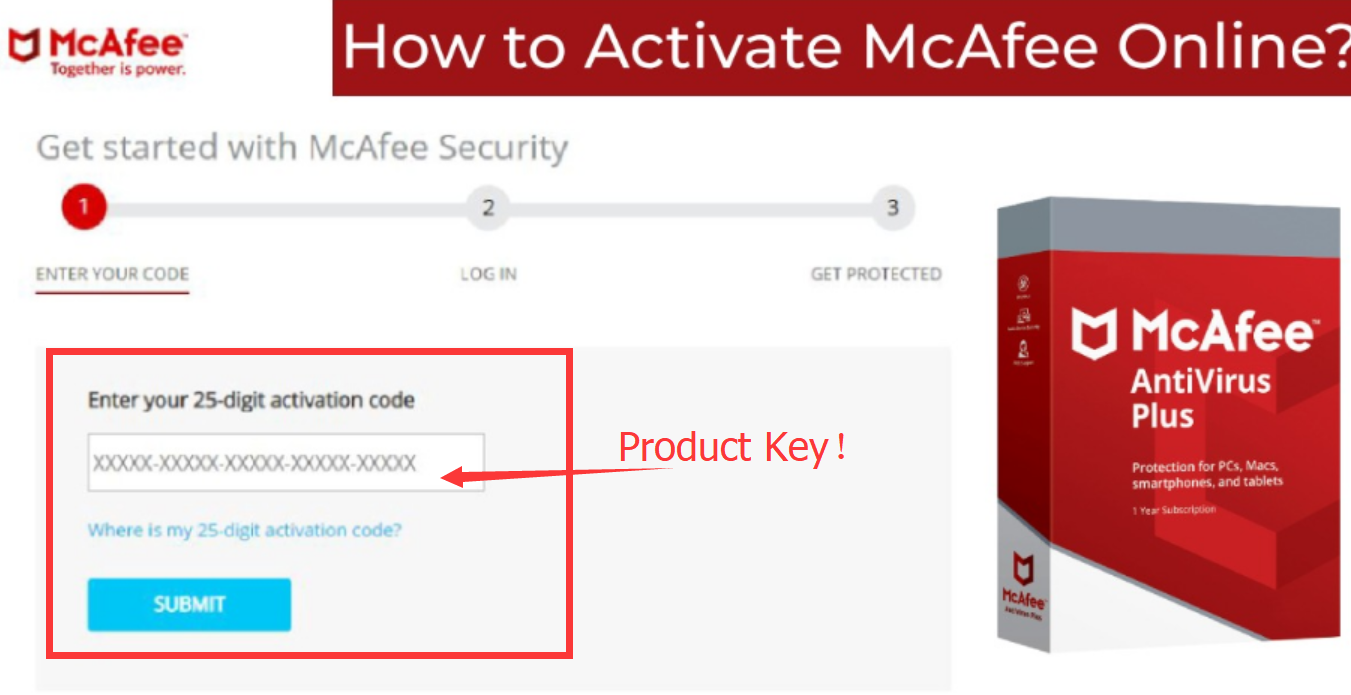
How to activate McAfee antivirus?
After installing the McAfee software, you will have to activate it. Without activation, the McAfee program will not work. You need to activate your McAfee product to display authenticity. You can activate your McAfee product by following the steps given here:
Online
- If you have purchased the McAfee product from the online store by going to “www.mcafee.com/activate“, then go to your email.
- In your registered email address, you will find a McAfee order confirmation email.
- Open that email and highlight the product key.
- Press Ctrl + C
- Launch the McAfee program.
- Paste the McAfee product activation key in the activation prompt.
- Click on the Activate button.
- If you get a prompt alerting you to activate the McAfee product, then click on it.
Offline
- If the user has bought the McAfee antivirus product from a retail store, then they can activate the code given on the McAfee retail card.
- The product activation key will be printed on the back of the retail card. The card will be provided with the installation kit.
- Copy the activation code.
 Go to the McAfee activation link mentioned on the card.
Go to the McAfee activation link mentioned on the card.- Choose your nation and language of preference.
- Type in the registration number of your McAfee product.
- Submit the product activation code.
- Click on Submit.
- At last, click on verify.
